In the digital age, where information reigns supreme, safeguarding data integrity isn't just a priority—it's an imperative. As the custodian of sensitive information, the onus falls on organizations to meticulously track and regulate access, fortifying the bastions of security through robust data access audits.
The importance of auditing the data access
Ensuring the proper access to sensitive data is a key fundamental security measure. In the same way, correctly logging and monitoring these access events is a crucial component of governmental and industry compliance. Without an effective data access audit trail, organizations open themselves up to both legal and security risks.
Regular data access audits are crucial in an environment where data centralization is key.
Understanding the Need for Data Access Auditing
The challenge with data access auditing
Performing an audit trail that correlates each data access event to a specific user poses a significant challenge. Many applications use connection-pooling, which masks the true identity of the end user, making tracking difficult. Also, auditing needs to cover all data access events, including read-only, data modification transactions, and privileged operations across all data systems containing regulated data.
So, what is sensitive data?
Sensitive data, also known as protected data, includes any information that can be deemed confidential and requires stricter security measures for protection. This data includes, but is not limited to, personally identifiable information (PII) like names, addresses, social security numbers, and credit card details, as well as private company data like internal reports, and financial or business strategy documents. Unauthorized access to such data can lead to severe repercussions like identity theft and financial fraud, or compromise of company competitiveness.
A Dive into Data Access Audit Log Structures

Consistent audit log structures and metadata
A consistent audit log structure and metadata are critical for analyzing data access events effectively. The structure should include action names, targets, action status, action status reasons, actor IPs, and session IDs. For start/end times for the query, policy sets, and support for DENIED logs, you might consider platforms like Immuta, which centralizes and simplifies filtering and analysis.
When a consistent log structure is being followed, auditing becomes significantly more manageable and accurate. The metadata gives context to the events, providing valuable insights into who accessed what data and when, and whether the event was successful or not. This forms the backbone of any audit trail, enabling effective root cause analysis and aiding in policy enforcement or adaptation.
Key capabilities required for successful log structuring
Successful log structuring requires some key capabilities:
- Consistency: All log events should follow a standard format for easy readability and parsing, with event details presented in a structured way.
- Clarity: Log entries should provide necessary information including user name, timestamp, action taken, data targeted, and outcome.
- Integrity protection: Any modifications to the log should be detectable to prevent tampering.
- Secure storage: Logs should be stored securely with restricted access to maintain confidentiality and integrity.
- Scalability: Arrangements should be in place to handle increasing volumes of log data over time without compromising performance or system efficiency.
- Queryability: Have a system that supports sophisticated querying and filtering of log data to aid accurate analysis.
Creating Detailed Audit Events
Essential elements of an informative audit event
A well-documented audit event captures all relevant details about the data access event. These essential elements include:
- Timestamp: The exact time and date when the data access event occurred.
- UserID: The identifier of the user or system account accessing the data.
- Data Object: The specific data object that was affected.
- Access Type: The nature of the data access — read, write, create, delete, or modify.
- Access Result: Whether the attempt was successful or failed.
- Source: Records the location from where the data was accessed, including IP address or terminal identification.
- Description: An optional but useful field where the user can input descriptive and contextual information.
Each component contributes to a clear picture that answers 'Who?', 'What?', 'When?', 'Where?' and 'How?' of a data access event, providing a comprehensive audit trail for forensic investigation, incident response, and compliance purposes.
Example: How to offer the most detailed event information audit
Mapping out detailed event information for auditing involves capturing each data access event in an extensive manner. Below is an example of an audit log entry captured using the SQL Server Audit feature:
`event_time: 2022-09-15 T 16:47:37.243action_id: SLsucceeded: 1user_name: DB_Userapplication_name: SQL Server Management Studioclient_ip: 172.16.255.255object_name: EmployeesTablestatement: SELECT * FROM [Human Resources].[Employees] where [EmployeeId] = 123`In this audit log entry:
- The `event_time` captures when the access event occurred.
- `action_id: SL` indicates that a SELECT Operation was performed.
- `succeeded: 1` shows that the access attempt was successful.
- `user_name: DB_User` shows who conducted the access.
- `application_name` tells us through which application the access was made.
- `client_ip` holds the information about the location (IP address) from where the request was made.
- `object_name: EmployeesTable` tracks the specific data object (table in this case) that was accessed.
- `statement` outlines the specifics of what action was taken; in this instance, corresponds to a specific employee record being accessed.
This approach gives the most detailed audit information, tracking each aspect of data access and aiding in forensic investigation and compliance checks.
Ensuring Audit Trails Integrity
Steps to ensure the trail audit integrity
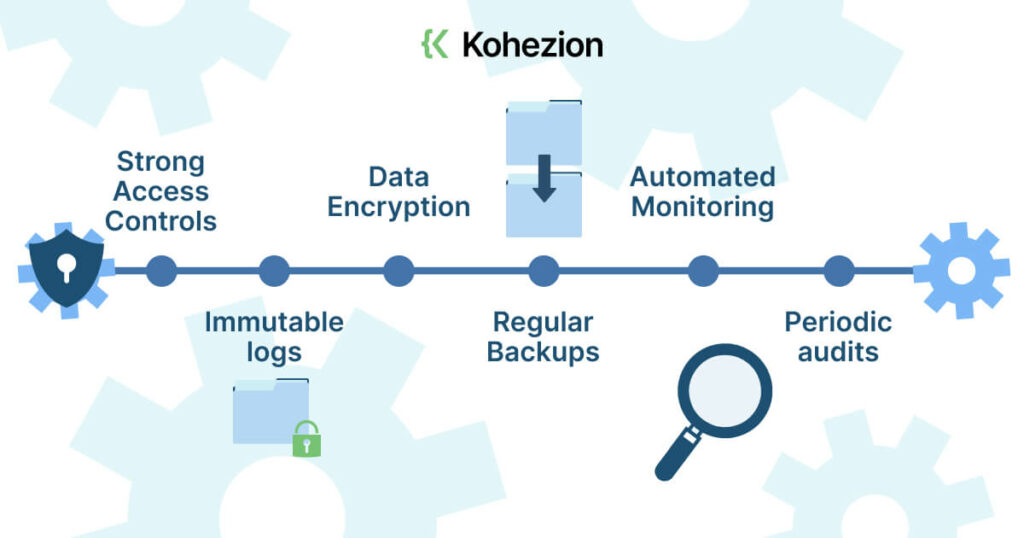
Maintaining the integrity of your audit trail is critical for ensuring it remains tamper-proof and reliable. Here are a few important steps to achieve this:
- Strong Access Controls: Restrict log file access to only a limited set of privileged users, minimizing the possibility of manipulation.
- Immutable logs: Implement a system where the logs cannot be manipulated or erased once written.
- Data Encryption: Encrypt log data both at rest and in transit to protect against unauthorized access.
- Regular Backups: Conduct regular backups and store them safely to prevent data loss.
- Automated Monitoring: Use automated tools to continuously monitor and alert about suspicious activities in real time.
- Periodic audits: Regular reviews of your logs can help identify potential discrepancies and secure the integrity of the audit trail.
Verifying that all audited systems are within the scope
Verifying that all audited systems are within the scope involves confirming that all systems that store, process, or transmit regulated data are included in the audit. Here are steps to ensure complete coverage:
- Inventory of Regulated Systems: Develop a comprehensive inventory of regulated systems that should come under audit scope. This includes databases, file servers, and any cloud storage that may contain the regulated data.
- Mapping Data Flows: Understand how regulated data moves within and outside the organization. Diagram the data flows to identify all touchpoints that should be covered by the audit.
- Implementing Controls: Ensure that there are adequate controls to monitor all data access points.
- Automated Discovery and Classification: Leverage tools for automated discovery and classification of database systems. This allows for quicker identification of systems and reduces the effort to maintain compliance.
- Regular Reviews: Regularly review the scope as systems and data flows may change over time.
How to have your data access logs ready for auditing
Step 1: Map out where your data is and how it's stored
The first step in preparing for a data audit is understanding where your data lives and how it's stored. This process involves creating a data map that outlines all databases, file servers, and cloud storage systems that contain regulated data. Note the type of information stored in each, along with details about the access controls in place and the frequency of data collection or updates. By the end of this process, you will have a comprehensive overview of your company's data architecture that will serve as a critical resource in the steps that follow.
Step 2: Take a deep look at what data you have and evaluate quality
Knowing what data you have on your hands and ensuring its quality is key. Begin with thoroughly examining your data's accuracy, breadth, and consistency - the ABCs of data quality. Carefully look out for any recurring errors and identify any potential gaps or inconsistencies.
Consider using a data quality tool that can aid in this process— these tools can detect formatting issues, duplicates, missing values, and other common problems. Also, speak to stakeholders and employees who interact with the data daily to gain crucial insights that will help you understand how and where to focus your quality improvement efforts.
Step 3: Make sure to audit all the sensitive data access
Sensitive data like personally identifiable information (PII), financial details, or strategic business information are prime targets for both external breaches and internal misuse. Therefore, ensure your audit trails cover all instances of sensitive data access. Key areas to focus on include:
- User Authentication: Who is accessing the data? Each data access event can be traced back to an individual.
- Access Type: What are they doing with the data? Monitor all types of data access, including read, write, update, or delete operations.
- Time of Access: When is the data being accessed? Determine whether access events occur outside of normal business hours, which could signal malicious activity.
- IP and Location: Where is the data being accessed from? This can help identify any abnormal login locations.
Step 4: Map out user accountability and create user-level event logs
User accountability provides your organization with a way to monitor and track individuals' actions within your systems. Building user accountability involves:
- Individual User Profiles: Rather than assigning team or departmental accounts, create individual user profiles for everyone accessing sensitive data.
- Access Levels: Define and assign access levels to avoid granting unnecessary permissions. This principle is often termed as "least privilege."
- User-Level Event Logs: Keep detailed logs with user-specific information for all data access events.
- Regular Reviews: Regular reviews of user privileges and behaviors identify any unusual patterns or habits and enhance accountability.
Step 5: Create customizable compliance reports, alertness tools, and analytical tools
To effectively prepare your data access logs for auditing, create customizable compliance reports, alert tools, and analytical tools.
- Customizable Compliance Reports: Tailor your reports according to your specific audit needs, whether they're internally required or for regulatory entities. Make sure these reports are easily presentable, comprehensible, and exportable.
- Alert Tools: Set up real-time alerts for any suspicious or anomaly in data access as part of your cybersecurity precautions. This can help you act swiftly in case of a potential breach.
- Analytical Tools: Analytical tools are necessary for reviewing the audit logs and identifying any patterns. They can help you spot trends, uncover gaps, and make evidence-based decisions for enhancing your security posture.
Step 6: Validate whether all the systems in scope are audited in the right way
Once you've set up your audit process, validate that all systems within the audit scope are audited properly.
To achieve this, follow these steps:
- Regular Verification: Periodically verify that your system inventory aligns with the audit scope to ensure all sensitive data areas are covered.
- Random Sampling: Audit a random selection of systems to verify the effectiveness of your audit process.
- Automated Checks: Utilize automation tools to verify your audits and reduce manual errors.
- External Audits: Consider having an external body audit your systems for an unbiased perspective on your audit process effectiveness.
Step 7: Offer the most detailed event information audit
To truly make your data access auditing robust, offer the most detailed event information audit possible. This includes:
- Identifiers: Capture all the identifying elements, such as UserID, IP address, terminal ID, and session ID to track who accessed what.
- Timestamps: Record the exact time and date of data access to understand when events occurred.
- Type of Operation: Detail the specific operation performed – reading, updating, and deleting data.
- Access Result: Note whether the operation was successful or failed.
Step 8: User access, user group access
User access and user group access refer to the roles and permissions assigned to individuals and groups within your organization. When you have a defined structure that outlines the access for each user and user group, you add an extra layer of security while simplifying your auditing process. Steps to follow include:
- Role-Based Access Control (RBAC): Define roles based on job responsibilities and assign them access rights. This can streamline access management, improve security, and simplify audits.
- User Group Access: If certain jobs share similar access requirements, group these roles together for ease of management. Be sure to log group-based activities as well as individual actions.
- Maintain a Master List: This list should detail each user (or group), associated roles, and the level of data access they’re granted. Update this list regularly to reflect changes in roles or access rights.
User Accountability & Access Control
Building and establishing user accountability

Establishing user accountability discourages misuse and ensures any inappropriate activity can be traced to the responsible individual. Key elements in building user accountability include:
- User Identification: Each user should have a unique identifier that leads back to them for all data access events.
- Role-Based Access Control (RBAC): Align access rights with job responsibilities. By doing so, individuals only have access to data they need for their role, minimizing potential data misuse.
- Audit Trails: Maintain a detailed audit trail that logs user activities. This promotes responsibility as users know their activities are traceable.
- Accountability Policies: Develop and communicate clear accountability policies to all employees. They should understand the expectations and possible repercussions of misusing access privileges.
Techniques to know who has access to what
Here are some techniques to achieve this:
- Access Control Lists (ACLs): ACLs define who can access data and what they can do with the data. Review these lists regularly and update them as roles change within your organization.
- User and Entity Behavior Analytics (UEBA): These tools use machine learning to track normal data access patterns and flag anomalies for review.
- Role-Based Access Control (RBAC): RBAC can be used to outline what data each job role can access.
- Automated Auditing Tools: These tools can help you keep track of who is accessing what data and can provide alerts if unusual activity is detected.
- Data Access Governance (DAG) Solutions: These solutions provide a clear view of data access permissions and usage within an organization.
Beyond Basics: Advanced Access Auditing Technologies
Analyzing enriched audit data at scale
Analyzing enriched audit data at scale involves diving into the audit logs efficiently and effectively to extract meaningful insights, trends, and patterns. Identify any unauthorized attempts or suspicious activities that might highlight vulnerabilities in your system.
Here's how to do it:
- Use Specialized Tools: Utilize data analytics or Security Information and Event Management (SIEM) tools like Splunk that can analyze large amounts of audit data rapidly.
- Automated Analysis: Implement automated analysis to quickly identify patterns and irregularities.
- Normalization of Logs: Aim to normalize your logs for consistency, making bulk analysis more feasible and meaningful.
- Enrich the Audit Data: Adding context to your audit data, such as tying IP addresses to specific geographical locations, can provide more enriched data for analysis.
Technology spotlight: Kohezion's security module that allows data access audit trails
Technology plays a pivotal role in effective data access auditing, and one such tool that stands out is Kohezion. Kohezion offers a well-structured security module, allowing you to create detailed data access audit trails with ease.
Why It Made the Best List:
- Ease of Use: Kohezion’s user-friendly interface makes it easy to create, track, and analyze audit logs.
- Scalability: It can easily handle large volumes of audit data, making it ideal for both small and large-scale businesses.
- Comprehensive Reporting: Kohezion provides detailed reports that can be customized based on the user's needs.
- Reliability: Used by a wide range of renowned organizations, its reliability has been well established.
- Affordability: Compared with other industry solutions, Kohezion delivers excellent cost-efficiency.
The Top 5 Features:
- User-friendly interface
- Scalability
- Customizable reporting
- Established reliability
- Good cost-efficiency
Cons:
- Hosted on the cloud, which might not be suitable for companies preferring in-house solutions
- Not suitable for businesses working with highly specialized or niche databases
Best For:
Kohezion is best suited for small and medium enterprises looking for a robust, affordable, and user-friendly data auditing solution, that can handle large volumes of audit data.
Conclusion
As our world relies more on data, safeguarding and overseeing it is key. Auditing ensures compliance, maintains data integrity, and strengthens security by minimizing unauthorized access and identifying breaches. It fosters transparency and user accountability within organizational data systems. This indispensable practice will evolve with technology, embracing better analytics, AI, and automation for more efficient audit processing. Cloud-based solutions will accommodate remote work trends. For organizations aiming for top-tier data security and compliance, data access auditing remains an essential and ongoing process.
Start building with a free account
Frequently Asked Questions
Auditing all access to sensitive data gives you the ability to understand who is accessing what data, when, why, and how. It's an integral part of maintaining compliance and preventing unauthorized access or data breaches. It enables you to detect anomalies, identify potential vulnerabilities, and improve security measures. It acts as evidence for compliance with data protection regulations, demonstrating accountability and transparency in your data handling processes. Without it, you leave your organization open to both security and compliance risks.
Ensuring the integrity of your audit trail involves protecting it from tampering or data loss. Implement strict access controls, so only authorized personnel can access the audit logs. Use encryption to protect log data and ensure logs can't be altered once written (immutability). Regularly back up your audit data to prepare for any unexpected situations. Monitor the logs continuously for any unusual activities and carry out regular audits to spot potential discrepancies. Lastly, consider deploying a centralized log management system for a more organized, secure, and robust audit trail.
Establishing user accountability involves several best practices. First, assign unique identifiers to each user. This helps track who is responsible for specific data access events. Next, implement Role-Based Access Control (RBAC) to align access privileges with job responsibilities, assign group accesses where necessary, and create user-level event logs. Regularly review assigned roles and behaviors and enforce a strict 'least privilege' policy, giving individuals access only to data necessary for their role. Lastly, define clear accountability policies and communicate them to all staff so they understand their responsibilities and the potential consequences of misuse.