According to the Verizon Data Breach Investigations Report, 80% of data breaches are the result of compromised login credentials. This fact shows the importance of data access control. As we deal with lots of sensitive data, having strong access control is not just good practice but a must for keeping data safe and following the law.
In this post, we’ll discuss the different types of data access control, its benefits, and how to implement it to improve your organization’s security.
We'll buid your first application for you. At no extra cost.
Let us build your first business application for free. Go from an idea to an application in under 2 weeks.

What is Data Access Control
Data access control refers to who can see or use data in a computer system. It's key to ensuring that only the right people can access certain data in networks or databases. Using strong access control mechanisms ensures that companies keep their data safe and manage it well.
Important parts include checking who users are and setting up access levels based on their roles or rules. These steps help companies follow the law and make sure data is used correctly.
| Aspect | Description |
| Authentication Mechanisms | Tools used to verify the identity of users accessing data. |
| Access Levels | Different permissions assigned based on user roles or organizational policies. |
| Data Governance | The management of data availability, usability, integrity, and security. |
| Compliance | Adherence to laws and regulations concerning data protection. |
| Security Measures | Practices implemented to protect data from unauthorized access or breaches. |
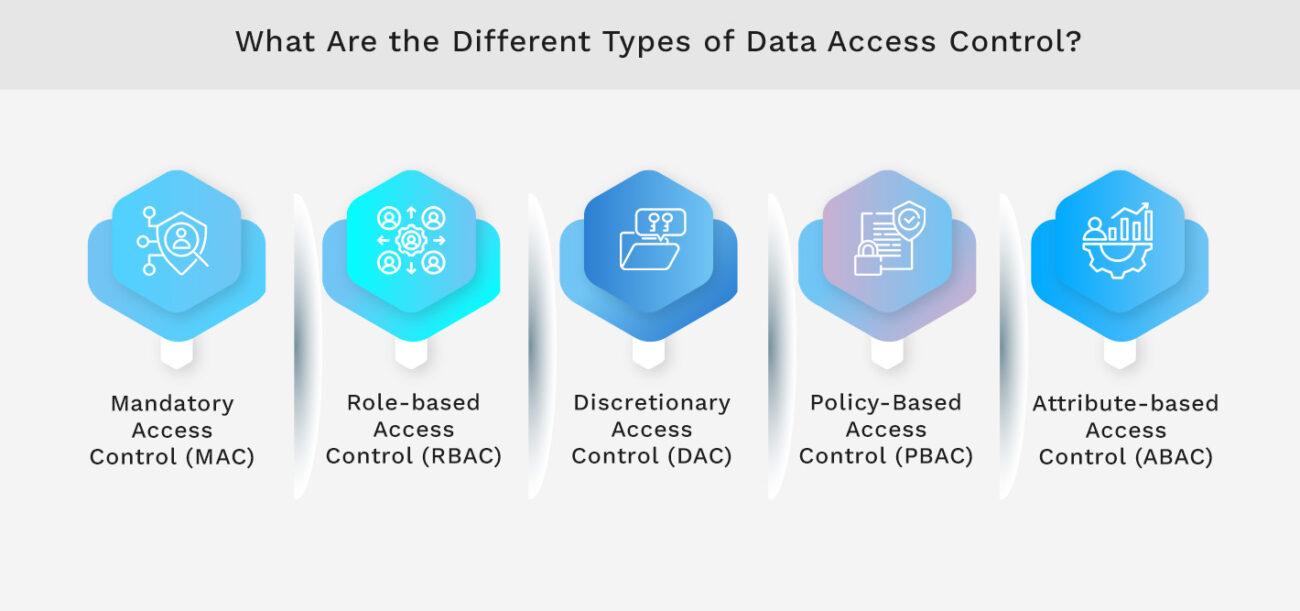
What Are the Different Types of Data Access Control?
Knowing about access control types is key for any group wanting to manage and keep data safe. You can pick the right system from options like MAC, RBAC, DAC, PBAC, and ABAC based on your needs.
Mandatory access control (MAC)
Mandatory Access Control (MAC) limits who can see certain data based on their clearance level and the data's level. A top person ensures no one gets to see things they shouldn't.
Role-based access control (RBAC)
Role-based access Control (RBAC) gives access based on a person's job in the company. It ensures that people only see what they need to, reducing the chance of data leaks.
Discretionary access control (DAC)
Discretionary Access Control (DAC) lets the person in charge of the system decide who can see certain data. This allows companies to create access rules that fit their specific needs.
Policy-Based Access Control (PBAC)
Policy-based access Control (PBAC) uses set rules to decide who gets access. It looks at more than just what someone does in the company; it also checks if they meet certain conditions before giving access.
Attribute-based Access Control (ABAC)
Attribute-based access Control (ABAC) uses user traits, data details, and the situation to make quick access choices. This method gives a lot of control and can handle the complex needs of modern companies.
Why is Data Access Control Important?
Data access control keeps sensitive information, such as personal data or trade secrets, safe from those who shouldn't see it. This can help companies significantly reduce the risk of data breaches.
Laws like GDPR and HIPAA require companies to control who can see their data. This lowers the chance of legal trouble and builds trust with clients and partners.
Strong data access control also improves a company's performance. It sets clear rules for who can do what with the data, which means employees work better without getting confused by unclear rules. It also leads to a more secure place for digital stuff.
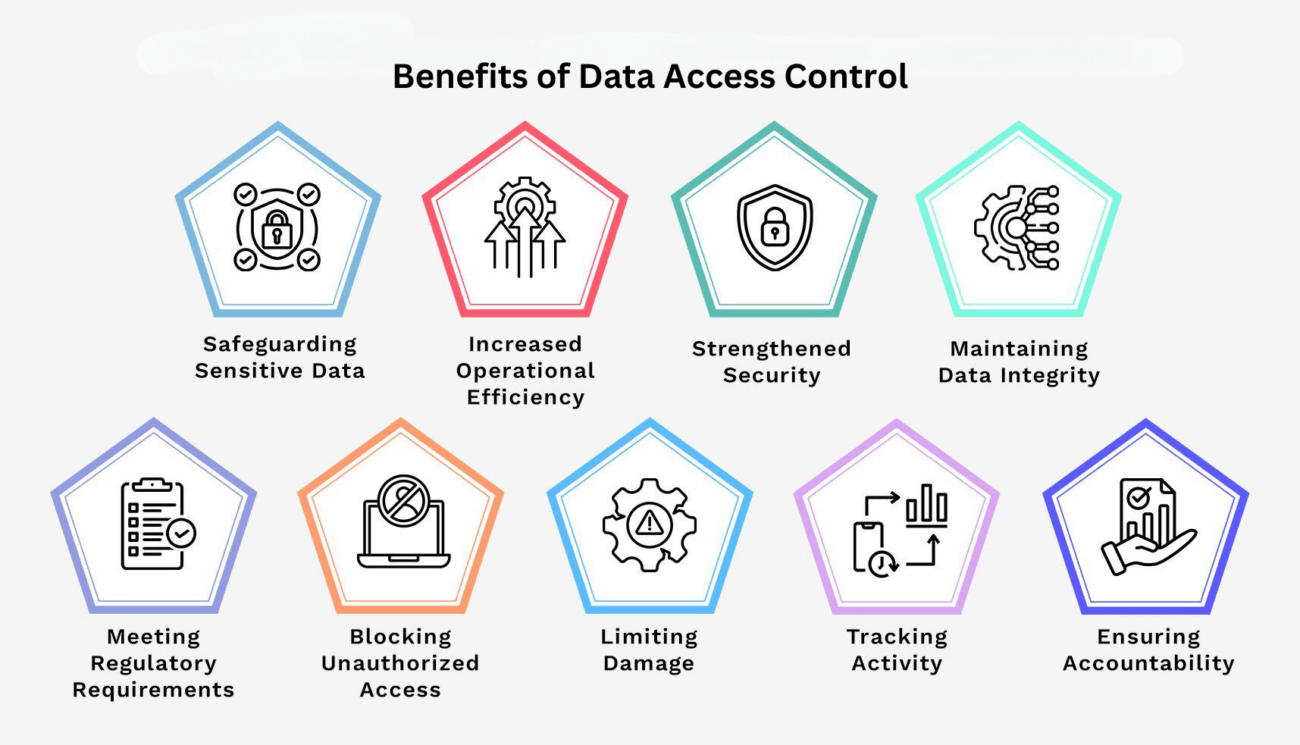
Benefits of Data Access Control
Data access control has big benefits for data protection and operational efficiency. It lets organizations control who sees sensitive data, helping lower risks and increase security.
Safeguarding Sensitive Data
Data access control acts like a shield. It ensures that only the right people can see sensitive information. This prevents data from getting out and being misused, making data protection key for any group.
Increased Operational Efficiency
When job roles limit access, things run smoother. This clears up confusion among workers and improves operational efficiency.
Strengthened Security
Having control over data access is key to fighting off security threats fast. It stops unauthorized attempts and strengthens security.
Maintaining Data Integrity
Data access controls keep information safe from changes or deletions by others, maintaining the data's trustworthiness and ensuring reliable data handling.
Meeting Regulatory Requirements
Reasonable data access control helps meet regulatory laws and requirements, improving data protection efforts.
Blocking Unauthorized Access
Data access controls cut down risks from both inside and outside threats. With strong security steps, it's easier to stop unauthorized access.
Limiting Damage
Limited access can lessen the harm from a data breach. Keeping information tight helps organizations better manage their sensitive data.
Tracking Activity
Logging who accesses data helps with monitoring and checking. This is key for security and running operations well.
Ensuring Accountability
Clear records of access help make users accountable. This supports good handling of incidents and encourages a responsible attitude towards data protection.
How to Implement Data Access Control
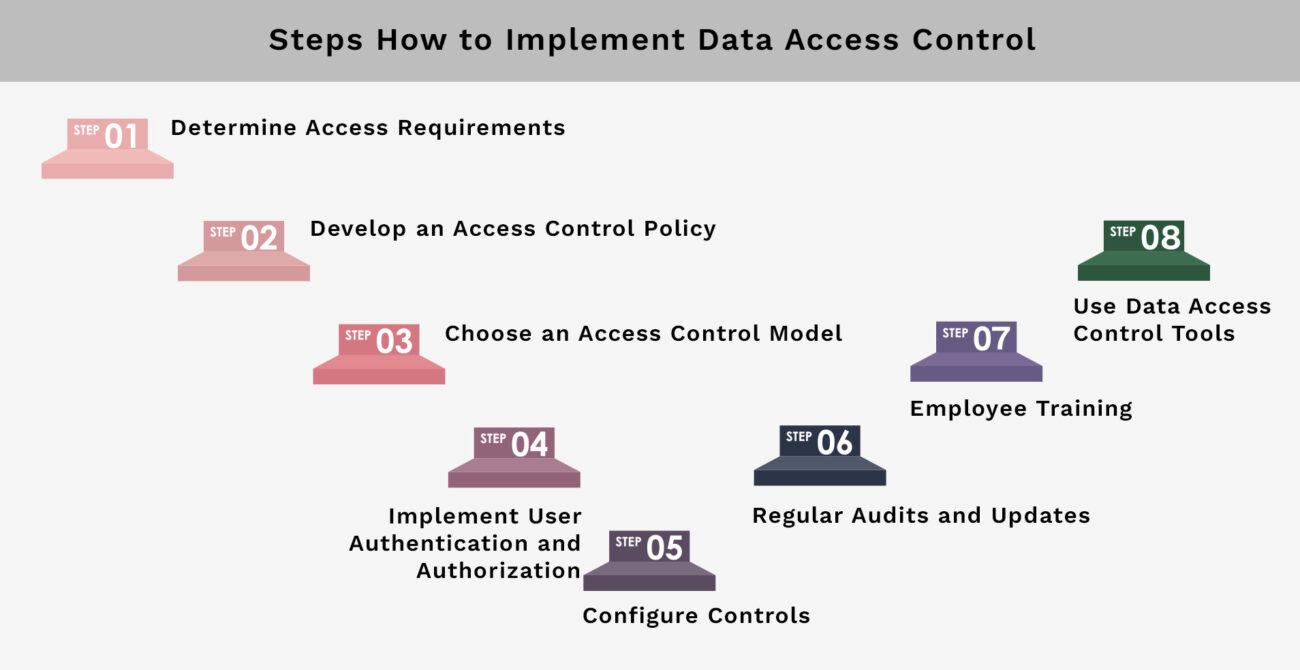
Implementing data access control is key to improving your organization's security. Here are the steps to take for successful implementation:
Determine Access Requirements: First, determine what data needs protection and who should have access. This step is the base for all other actions.
Develop an Access Control Policy: A detailed policy should clearly state who can do what, follow what rules, and how to keep data safe. This policy will help grant and manage access.
Choose an Access Control Model: Pick a model that fits your company's structure and the data you handle. Options include Role-Based Access Control (RBAC) or Discretionary Access Control (DAC).
Implement User Authentication and Authorization: Create strong ways to check who you are and what you can do. Good authentication lowers the chance of unauthorized data access.
Configure Controls: Set up controls based on your chosen model. This means giving roles and permissions that match the access needs you've set.
Regular Audits and Updates: Check your access settings often. Regular checks make sure access control works well and changes with new staff or data types.
Employee Training: Teach your team about data protection, security risks, and how to stay safe. Knowing how to protect data will help you reduce mistakes and improve security.
Use Data Access Control Tools: Use tools like Identity and Access Management (IAM) systems. These tools help you see and control who gets to access data, making it easier to manage.
Kohezion Can Improve Your Data Access Control
Kohezion offers powerful tools to improve data access control. Its data access solutions make managing access to databases and data warehouses easier, which is great for ensuring your data is secure and follows the rules.
The platform lets you set customizable user permissions based on job roles and the sensitiveness of the data. This way, you can give the right access to the right people while keeping data safe from unauthorized access.
Kohezion's real-time monitoring lets you monitor who sees what data. This helps your organization stay secure and follow the rules. Using Kohezion's tools strengthens data access control and encourages a secure work culture.
Conclusion
Proper data access control makes sure only the right people can see important data. This helps lower the risk of unauthorized access and keeps your business's good name safe.
It's not just about keeping data safe. Access control also helps meet the rules of many industries and ensures you stay compliant.
Good data access control makes your business run better and more responsibly. It helps your organization work well while keeping risks low. Following the best practices in data access control ensures that companies keep their data safe and do well. Staying strict with access rules helps your business stay strong against growing cyber threats.
For more information on how Kohezion can help you improve your data access control and protect your business, please contact us today.
Start building with a free account
Frequently Asked Questions
Data access control provides a secure environment where users can trust that their data is safe, which leads to a better user experience. However, if not implemented properly, it can slow down access to needed information or cause frustration if users don’t have the correct permissions. Balancing security and usability ensures a positive user experience while maintaining robust access controls.
Encryption converts data into a coded format that unauthorized users cannot read. Even if someone gains access to the data without permission, they cannot understand or use it without the decryption key. Encryption adds an extra layer of security, ensuring that sensitive information remains confidential and safe from prying eyes.
Without proper data access control, organizations risk unauthorized access to sensitive data, leading to data breaches, loss of customer trust, and potential legal penalties. It can also result in data manipulation or theft, which can harm a company’s reputation and finances. Lack of control makes it difficult to track who has accessed or changed data, leading to accountability issues and increased vulnerability to cyberattacks.
