What is Single Sign-On (SSO)?
Single Sign-On (SSO) allows users to log in with a single ID and password to access multiple applications, systems, or services. With SSO, you no longer need to juggle multiple passwords. Instead, SSO allows you to navigate through your suite of tools and platforms with ease.
How Does SSO Work?
SSO checks your ID once and then grants you entry to all the services your credentials can access. When you input your SSO details, an authentication server verifies your identity, issues a token or ticket, and shares this with various applications.
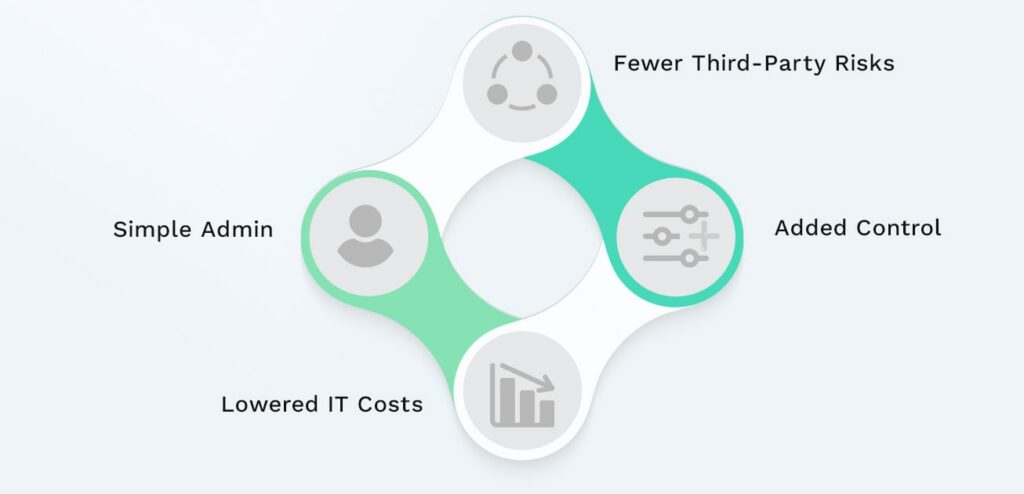
Benefits of SSO Database
Embracing SSO in your digital framework comes with many benefits, including fewer third-party risks and lowered costs. This is not lost on the Single Sign-on market which was valued at $1431.5 million in 2023 and is expected to grow to $3390.9 million by 2030.
Fewer Third-Party Risks
SSO lowers the chances of unauthorized access or data breaches by limiting access points to third-party systems. With SSO, there are fewer connections to outside systems, which means there are fewer chances for something to go wrong. It simplifies the process of checking and keeping track of these connections, making it easier to ensure everything is secure. This helps companies protect their data and systems better when interacting with outside parties.
Added Control
SSO provides administrators with a centralized system for managing user access, allowing them to set specific permissions and restrictions easily. This means they can control who has access to what information and applications within the organization. Having a single point of control makes it easier to monitor and enforce security policies across the board. Additionally, SSO enables administrators to revoke access quickly and efficiently when needed, enhancing security measures. This added control provided by SSO helps organizations better manage their digital resources and safeguard sensitive data.
Lowered IT Costs
Implementing SSO databases can save a lot of money. A study by Gartner found that between 20% and 50% of all help desk calls happen because of password problems. Another study by Forrester showed that fixing a password issue costs organizations about $70 per fix. SSO helps cut down on help desk costs by only needing one password. With fewer calls about passwords, IT staff can concentrate on more important tasks.
Furthermore, with SSO, there is less need for multiple authentication systems, streamlining the IT infrastructure and leading to savings in hardware, software, and maintenance costs. IT teams also spend less time training on multiple systems, which translates to reduced training costs. Lastly, the reduced number of systems and platforms allows companies to negotiate better deals due to bulk purchasing.
Simple Admin
The administration of a Single Sign-On database architecture is straightforward and user-friendly. Administrators now have a unified dashboard from which they can manage accounts, control access rights, and monitor user activities across various applications with ease. Onboarding and offboarding users are more efficient, and any changes made in the system apply instantly across all connected applications.
This setup also makes auditing easier by providing a single point for tracking authentication events. It reduces complexity by using fewer tools and protocols, which means administrators don't need as much technical knowledge. Overall, it makes the daily tasks of administrators easier and removes the complications of managing multiple admin consoles.
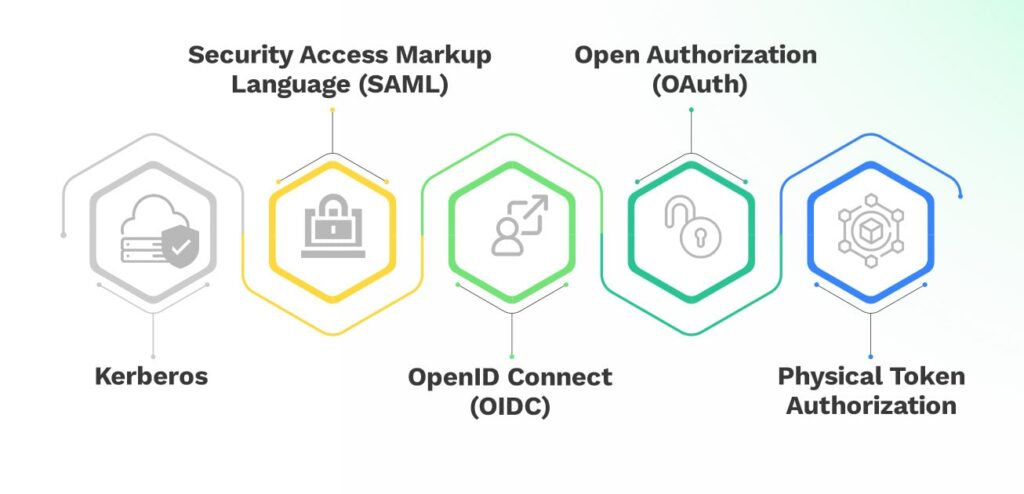
Types of SSO
Kerberos
Kerberos is a network authentication protocol that works behind the scenes to manage user credentials and ensure secure access. The process follows a system where a "ticket-granting ticket" (TGT) leads to service-specific tickets, allowing users to access network services without repeatedly entering passwords. These tickets have a limited lifespan, enhancing security by minimizing the risk of stolen credentials being used.
Kerberos also implements mutual authentication, where both user and service verify each other's validity, thus combatting impersonation attacks. Furthermore, it employs robust cryptography to safeguard credentials during transmission and requires minimal client storage, reducing client-side security risks. Kerberos shines in closed network environments, such as within corporate intranets, where control over all elements of the system is possible. It's robust, low on resource usage, and when configured properly, is a bastion of the SSO ecosystem.
Security Access Markup Language (SAML)
Security Access Markup Language (SAML) is a protocol designed for web-based applications. SAML communicates through XML, which is versatile and widely supported, making it platform-independent. It supports federated identity, allowing for shared authentication across different organizational boundaries.
SAML passes security assertions or statements that validate a user's authentication and authorization status, enhancing security measures. Additionally, SAML enables single-click access to multiple web-based resources, improving user satisfaction. SAML particularly excels in use cases where SSO needs to span across multiple domains, which traditional protocols may not handle well.
OpenID Connect (OIDC)
OpenID Connect (OIDC) builds on the foundation laid by OAuth 2.0, focusing on identity verification. It's perfect for web and mobile applications, providing a secure identity layer for easy access without the need for repetitive logins.
OIDC adds a verified user identity to OAuth's authorization framework, providing both authentication and authorization. This system operates on a token-based mechanism, using JSON Web Tokens (JWT) to securely encode user information for transmission between parties.
Standardized claims are used to share information about the authenticated user while OIDC defines an endpoint that provides data about the authenticated end user, enabling richer user profiles. Its design is optimized for modern application environments, including mobile apps and single-page applications (SPAs), making it a preferred choice for developers seeking seamless integration with newer platforms and a more flexible user authentication schema.
Open Authorization (OAuth)
Open Authorization, commonly known as OAuth, facilitates secure delegated access, allowing applications to acquire limited access to user accounts on various services. It's what powers features like "Log in with Facebook" buttons, prioritizing user convenience and privacy protection.
OAuth allows users to grant third-party access to their resources without sharing their credentials. It operates with granular permissions, so applications only get the access they need, which is determined by predefined scopes.
OAuth uses access tokens rather than user credentials, adding a layer of security. The protocol also supports extensions for better integration with other standards and systems.
OAuth allows services to communicate and act on a user's behalf while maintaining strict controls over what they can see and do. It strikes a balance between user convenience and security making it indispensable in the interconnected app ecosystem.
Physical Token Authorization
Physical Token Authorization hands the power of access to a physical device like a key fob or a smart card that generates a passcode used in combination with a PIN or password. Some tokens include fingerprint or retina scanners for added security, ensuring the person holding the token is the authorized user. Smartphones can also act as tokens, using apps to generate codes or receive prompts for user confirmation.
Physical token authorization is highly secure because it involves a physical object that would be difficult to duplicate or obtain covertly. On the downside, users must carry the token with them and it can be easily lost or stolen.
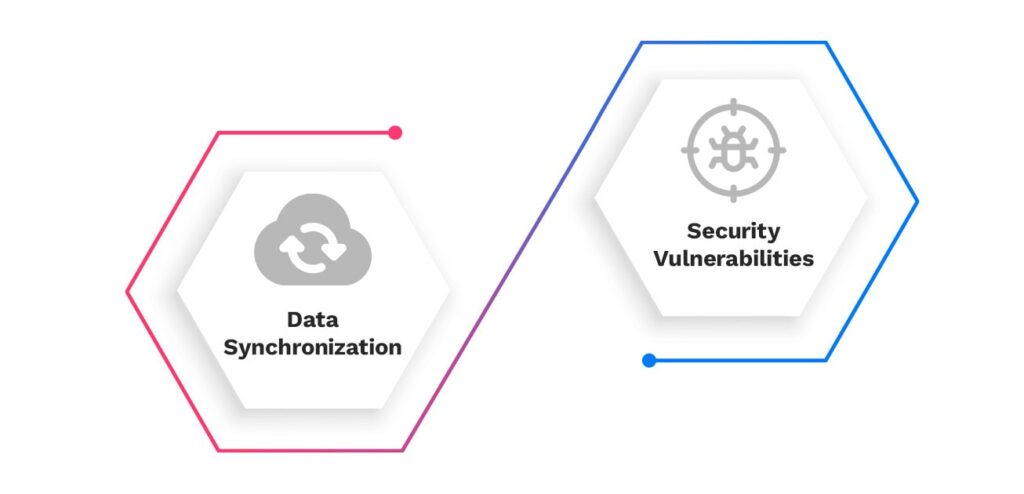
Challenges of SSO Database
Data Synchronization
When using Single Sign-On, data synchronization is very important for maintaining a cohesive and up-to-date user database across different platforms. Consistency across platforms ensures that when a user's information changes on one service, the update cascades through all associated systems. Synchronization often occurs in real time or within scheduled intervals, minimizing discrepancies in user data. Good SSO includes mechanisms to handle conflicts when the same data is altered in two places simultaneously.
Synchronization simplifies user management by automatically activating and deactivating user access across services. Additionally, keeping an accurate and up-to-date log of data changes helps with compliance and security auditing.
However, improperly managed data synchronization can lead to issues such as outdated access rights, inconsistent user experiences, or data integrity problems. That’s why administrators must ensure that robust synchronization strategies are in place.
Security Vulnerabilities
SSO provides convenience and a streamlined user experience but it is not without potential security vulnerabilities. The centralized nature of SSO means that if a user's credentials are compromised, unauthorized access could potentially be gained to all connected applications.
SSO can be susceptible to phishing, where attackers trick users into revealing their SSO credentials. Session hijacking is also possible, where an attacker gains control of a user's SSO session token and then impersonates the user across all associated applications. Lastly, malicious scripts injected into web pages can potentially hijack SSO sessions or redirect users to fraudulent authentication pages.
Mitigate these risks by implementing strong security measures, such as multi-factor authentication, regular security audits, encrypted session tokens, and user education on recognizing phishing attempts.
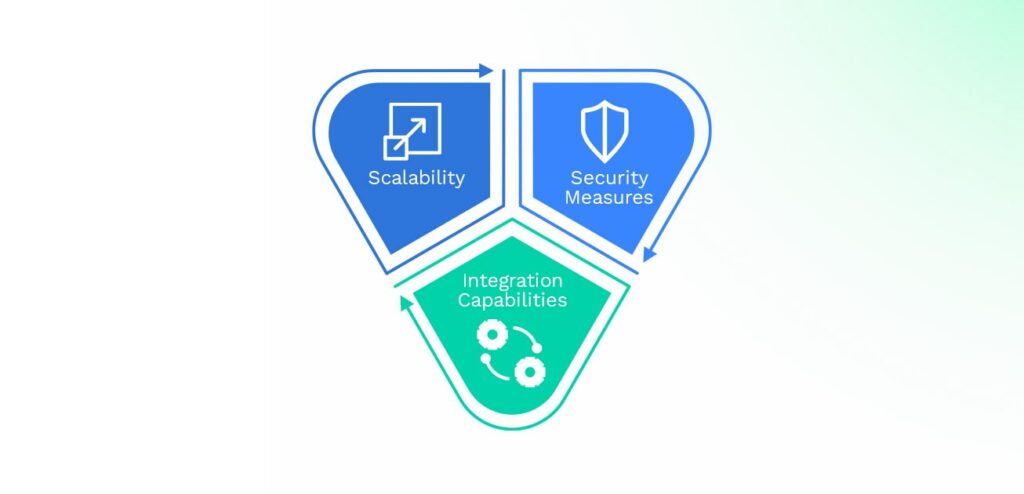
Factors to Consider When Setting Up an SSO Database
Scalability
When setting up an SSO database, consider how well the system will grow with your organization. Scalability ensures the SSO can handle the increasing load you expand, including more users, more services, and more access requests without a drop in performance.
The SSO solution must comfortably accommodate the number of concurrent user sessions as your user base grows. It also needs the capacity to integrate with a growing number of applications, both on-premises and in the cloud.
Look for SSO solutions with a global deployment to ensure that the system performs well across different geographic regions if you expand internationally. The ideal SSO database should also have a modular design that can be expanded or modified as required.
Choosing an SSO database that's built to scale ensures a positive user experience, sustains administrative efficiency, and helps avoid costly overhauls as your needs develop over time.
Security Measures
Security measures are essential for defending against cyber threats. According to research, passwords account for more than 80% of all security breaches, allowing hackers to access a company’s systems or steal identities. That’s why you need to investigate the SSO service security policies before you commit.
The SSO service must encrypt data both at rest and in transit to shield against interception and unauthorized access. Having multi-factor authentication (MFA) further enhances security, and regular security audits help identify potential vulnerabilities before they can be exploited.
Check also if the SSO provider adheres to recognized security standards like ISO/IEC 27001 and SOC 2 and whether proper session timeout policies and token revocation mechanisms are in place to prevent unauthorized access.
Integration Capabilities
Assess the integration capabilities of an SSO database to make sure that it can harmonize with the various applications and systems already in use within your organization, both in-house and third-party.
Robust APIs are a must for creating custom integrations and ensuring smooth communication between systems. The SSO solution must also comply with industry standards like SAML, OIDC, and OAuth for smoother implementation and interoperability.
Look for the ability to adjust authentication flows and user interfaces to fit your specific organizational needs. Lastly, ensure that the SSO solution offers intuitive tools that make it easy to add new services or modify existing integrations.
Selecting an SSO with strong integration capabilities means less hassle down the line, creating a cohesive and secure user experience that can adapt to your evolving business requirements.
Create Your SSO Database with Kohezion
Create Your SSO Database with Kohezion and empower your users with a seamless login experience across multiple applications. Our custom SSO solutions are designed to enhance security, reduce password fatigue, and simplify user management.
With Kohezion, you gain a robust, centralized authentication system that aligns with your business’s unique requirements, ensuring that your data remains protected while offering users the convenience they expect in the modern workspace.
Conclusion
SSO technology is a game changer for modern businesses, offering a range of benefits in security, productivity, and user satisfaction. SSO alleviates password fatigue by enabling users to move effortlessly between services using a single set of credentials. It also empowers IT admins with more streamlined, effective management tools.
Understanding the various types of SSO and carefully considering factors such as scalability, security measures, and integration capabilities helps organizations craft robust, future-proof authentication systems.
As you step forward with SSO, remember it's a delicate balance between user convenience and cybersecurity. Keep these insights in mind and you'll be well on your way to creating an SSO solution that's both user-friendly and ironclad.
Take the hassle out of managing multiple logins and ensure data security with Kohezion's intuitive platform for creating a powerful Single Sign-On (SSO) database - book a training and start optimizing your authentication workflow today!
Start building with a free account
Frequently Asked Questions
Databases that feature robust access control, support for industry-standard protocols (like SAML, OIDC, and OAuth), and have strong encryption capabilities are best suited for SSO implementation. Examples include SQL Server, Oracle, and MySQL because they offer the necessary security features and are widely supported by SSO solutions.
Ensure the security of your SSO database by implementing multi-factor authentication, using strong encryption for data at rest and in transit, regularly auditing your systems, and ensuring compliance with security standards. Educate users on secure practices as well.
Yes, implementing SSO can save time and resources for your organization. It streamlines user access management, reduces password reset requests, and minimizes the effort and cost associated with maintaining multiple authentication systems.

